So now let us look at an example where we will have data going back and forth between 2 parties. Let’s take the following example: a user (let’s call him Han) wants to do stock trading via the website of his bank.
Knowing very well that the cyber arena has no shortage of criminals who just cannot wait to get their hands on our information, we will obviously encrypt our communication (data) that is going over the line to our bank’s website. The encryption we have already touched on should do the trick. After encrypting the data, we are ready to send it off to the bank’s web server. But how will the bank know how to decrypt the data?

This implies that we need to enable the bank’s website to decrypt our message. We thus need to find a way to send/notify the bank on how they should decrypt the data. But wait, how will they even know how to decrypt the data without knowing the key. Enter Public and Private key cryptography or asymmetric cryptography!
Boiled down, the whole public and private key cryptography technology pivot on two unique big numbers. As you might recall from symmetric or even with the Caesar cipher, the key that was used to encrypt/decrypt the data is the only key that is able to decrypt the data. And this is where asymmetric cryptography differs! The magic here is that these 2 big numbers (1024 or 2048 bit, more appropriately referred to as keys) that are mathematically related to each other in such a way that it is possible to encrypt with one of the 2 keys and being able to decrypt with the other. Never the same key!
Assume we have the following keys:
- Key A
- Key B
The important thing to remember here is:
- You are able to encrypt with A => decrypt with B (NOT with A!)
- You are able to encrypt with B => decrypt with A (NOT with B!)
A good analogy for the working is to visualize either of these keys as a type of vault/safe.

This means that when you get to send this safe (let’s say the public key in this case) and as soon as you have encrypted the message you cannot get it open again. Try and visualize this as an open safe you received from the bank. The door is open so you can put your secret message in it, then close the door and lock it by spinning the combination dial. BUT you (or any other person) does not know the combination to open it again – only the Bank knows that! So you then send off the safe to the Bank. As soon as it gets there, they know the combination to open it, and can retrieve your secret message. So back to the keys, in a sense, it works very similarly. You can lock (encrypt) the message on your side, but you cannot get it open again – only the keeper of the other key can. The only person that can get it open again is the person that is in possession of the other key – the private key in this case.
Where do we get these very clever keys?
Again the simplicity baffles, they are just generated. There are numerous ways to do this, tools, third-party libraries etc. After you generated the two keys (remember that they are just 2 keys at this stage), the next step is to decide/pick which one you want to share with the world and which one you wish to keep secret. We need a key that we will make public (everybody may have this) and one that we keep private (MI6 style secret)
The keys look something like this:
—–BEGIN RSA PRIVATE KEY—–
MIICXQIBAAKBgQCy8627yI4hMwdoUD6M/VJQ090Ec6uhv2bqMmAXXB9scr8SvGr/
9I+5ZWNmzdX7AvX3TblD+e9M0oNO4AVnXSlmOAKplY8N2q09Vrllr2+Lkq69qOfp
fIuk+fwQXOiGJk4UWk4b2dkq9XYmZYCgaeKD4w3S35btCg9npK3GHmK1TwIDAQAB
AoGBAJCwX+9uCCUluj6IaxraE71Qn+pikAo21MJVOsaIcMvht0Yx3B3Zon+XT5im
ovXSfgeX60zf/7FQoGSc0yGw/K/SXYyU+PCGNTMYEFvz0is5qdjQPSqjiKsYUTSu
HiOjQouvwqTgTIK1KZme+/KcnxiHuXGsAJy2hh4xcwE0mMDhAkEA7c+3BJSGnRcI
8rWwl3S+BwEgyIYxOTsTKr9S0i1xdvEgU7RCk7Ef1VjgrVhCvaCg+zwK1vVvgFc1
onSywFTP0QJBAMCjgnwok6ktv30zvm05uWBO55cny1yyQg+lL5mWawaw2hmiX2mP
9lzRGFx/YKuYzvQeqvoNwj3e4UvKl8Iqmx8CQQDnV2vJLtuNMf1obsttawn5MmW7
7J8x93/708cz4zU/6e3yv6cMmgBHwYA/4V57riksfgpldrmTdkMc2L2TUG4hAkAt
rliCAslJRAz1rrCIjDi2at+mS4yA9dCOjzhjbnUAyC1gCM4hZT8hsX/aZ2ZQKtNg
tmkLFPor28+HPoqQQ7Q3AkAZ2NM7Q4O+VA6PEKtHAqFtnhPOzD0P+M+dIcWJoMJf
/eg4M0buBg6UStUFvcw1QSAYtJ/C9UFXYuP32Uo0alV5
—–END RSA PRIVATE KEY—–
—–BEGIN PUBLIC KEY—–
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCy8627yI4hMwdoUD6M/VJQ090E
c6uhv2bqMmAXXB9scr8SvGr/9I+5ZWNmzdX7AvX3TblD+e9M0oNO4AVnXSlmOAKp
lY8N2q09Vrllr2+Lkq69qOfpfIuk+fwQXOiGJk4UWk4b2dkq9XYmZYCgaeKD4w3S
35btCg9npK3GHmK1TwIDAQAB
—–END PUBLIC KEY—–
We already learned that the public key is accessible to everybody. Let’s take the following scenario to grasp how it will work in small steps.
- Han – The user that wants to communicate securely with his bank.
- Bank – Also wants to communicate securely with their client Han.
So first of both Han and the Bank need to create a set of keys. After they have generated these they will identify one to be a public and the other to be the private key.

The next step is to get your public key out there (public) i.e. get it distributed in order for it to be accessible to the outside and enabling people to use it. This can be accomplished in numerous ways – published on a website, end of emails etc. We will keep it simple and just send the keys to each other.
- We will get the bank’s public key
- We give the bank our public key

After we have exchanged public keys, we are all set to encrypt some data!
Notice in the picture below that we have now exchanged public keys. Han has the Bank’s public key and the Bank has Han’s public key. We will be assuming that Han will take the first step to send some data to the bank. He will thus use the Bank’s public key to encrypt plaintext data to ciphertext.

After that was done, he can send the ciphertext over the line to the Bank. If someone is to eavesdrop on this, they will not be able to do anything with the data as it is gibberish and unreadable to them without having the matching private key.
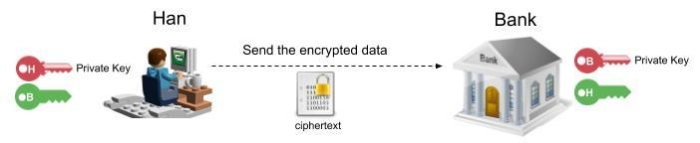
As soon as the bank has received the encrypted data it will proceed in decrypting it. This is of course done with the ‘magic’ that asymmetric keys provide us with. The matching private key, that is only known to the bank, is able to decrypt the data!

This is the essence of the encrypt/decrypt cycle in asymmetric encryption in nutshell! Of course there are some extra things that happen on the fringes, but in my opinion, this is the core message of it.
One thing to keep in mind, considering the flexibility that Asymmetric encryption provides us, is the area of performance. Symmetric encryption as was discussed in the previous section outperforms Asymmetric encryption!
Pretty secure one would think, but where there is a will, there is a way. Let’s have a look at an example where an attacker can still misuse this technology to their advantage. Read it here.
